Computer Networking Security Guide: Digital Infrastructure
In today’s connected world, computer networking security has become a cornerstone of every organization’s IT strategy. From small businesses to large enterprises, securing network systems is no longer optional. it’s essential. This Computer Networking Security Guide explains everything you need to know about protecting your network, common threats, and best practices to keep your systems safe.
What Is Computer Networking Security?
Computer networking security refers to the policies, practices, and technologies designed to protect data, devices, and systems connected to a computer network. It involves preventing unauthorized access, detecting breaches, and maintaining the integrity and confidentiality of digital assets.
A secure network ensures that only authorized users and devices can access sensitive information and that your system remains safe from cyberattacks, malware, and data leaks.
Why Network Security Is Important
The importance of networking security cannot be overstated. As businesses increasingly rely on cloud computing, remote work, and digital collaboration tools, the attack surface for hackers grows. Here are some key reasons network security is vital:
- Protection Against Cyberattacks: Hackers constantly target networks to steal data or disrupt operations.
- Safeguarding Sensitive Data: Prevent data breaches that can result in financial and reputational damage.
- Compliance Requirements: Industries like healthcare, finance, and government require strong security measures to meet legal regulations.
- Maintaining Productivity: Preventing downtime due to malware or ransomware attacks ensures smooth business operations.
- Building Customer Trust: Clients trust companies that can protect their personal and financial data.
Common Network Security Threats
Before securing a network, it’s crucial to understand the common threats that can compromise it. These include:
1. Malware and Viruses
Malicious software can infiltrate a network through email attachments, infected websites, or downloads. Once inside, malware can corrupt files, steal data, or damage hardware.
2. Phishing Attacks
Cybercriminals send fake emails that trick users into revealing login credentials or clicking malicious links.
3. Ransomware
This type of malware locks files or systems until a ransom is paid. Ransomware attacks are one of the most damaging threats today.
4. Denial-of-Service (DoS) Attacks
In a DoS attack, hackers flood a network with traffic, overwhelming the system and making it inaccessible to legitimate users.
5. Man-in-the-Middle (MitM) Attacks
In these attacks, a hacker secretly intercepts communication between two systems to steal or manipulate data.
6. Insider Threats
Not all threats come from outside. Disgruntled employees or careless users can unintentionally compromise security.
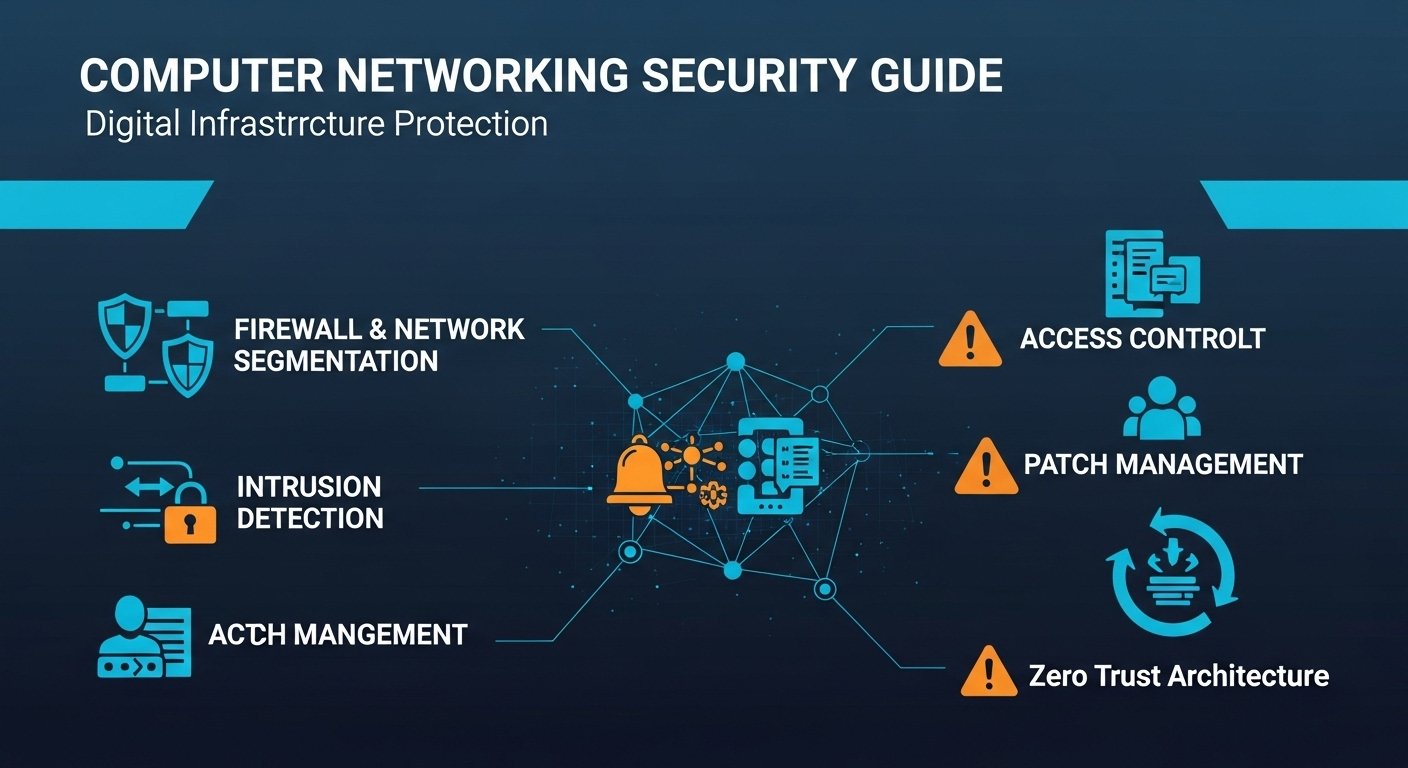
Essential Components of Computer Network Security
A strong network security strategy relies on multiple layers of protection. The most important components include:
1. Firewalls
Firewalls act as the first line of defense by monitoring incoming and outgoing traffic. They block unauthorized access while allowing legitimate communication.
2. Antivirus and Anti-Malware Software
These tools detect, quarantine, and remove malicious software before it can harm your network.
3. Intrusion Detection and Prevention Systems (IDS/IPS)
IDS/IPS solutions monitor network activity for suspicious behavior and can automatically block potential threats.
4. Virtual Private Networks (VPNs)
VPNs encrypt internet connections, making it difficult for hackers to intercept data transmitted over public or unsecured networks.
5. Encryption
Encrypting sensitive data ensures that even if it’s intercepted, it cannot be read or used by unauthorized parties.
6. Access Control
Restricting access to systems and information ensures that only authorized personnel can view or modify sensitive data.
7. Regular Software Updates
Keeping all operating systems and applications up to date helps close security loopholes that hackers might exploit.
Best Practices for Network Security
Implementing network security is not just about installing software. it’s an ongoing process. Here are the best practices every organization should follow:
- Create Strong Password Policies:
Enforce complex passwords and require regular updates. - Use Multi-Factor Authentication (MFA):
MFA adds an extra layer of security, even if a password is compromised. - Regularly Back Up Data:
Maintain backups to recover quickly from ransomware or system failures. - Segment the Network:
Divide networks into smaller parts to limit access and contain potential breaches. - Educate Employees:
Human error is a major cause of security breaches. Regular training helps employees recognize phishing and other threats. - Monitor Network Traffic:
Continuous monitoring helps detect unusual behavior before it becomes a serious issue. - Implement Strong Security Policies:
Define clear rules about device usage, remote access, and data sharing within the organization.
The Role of Cloud Security
With the rise of cloud-based storage and services, cloud network security has become an integral part of overall protection. Cloud providers offer built-in security tools, but organizations must still configure firewalls, encrypt data, and monitor access to ensure full protection.
Hybrid and multi-cloud environments especially require advanced solutions such as zero-trust architectures, automated threat detection, and encryption across all layers.
Future of Computer Network Security
As cyber threats evolve, so must network security. Emerging technologies like Artificial Intelligence (AI) and Machine Learning (ML) are being used to predict, detect, and respond to attacks in real time. Additionally, Zero Trust Security Models — where no user or device is trusted by default — are becoming the new standard.
Quantum computing and 5G networks will also reshape how organizations approach network protection, requiring more advanced encryption and faster detection systems.
Conclusion
This Computer Networking Security Guide highlights how essential it is to protect digital networks in today’s world. Cyber threats are constantly changing, and businesses must stay vigilant by implementing layered security, regular monitoring, and employee training.
Network security isn’t a one-time task. it’s an ongoing commitment to safeguard your data, systems, and reputation. By following the best practices and using modern tools, you can create a secure network environment that supports your business growth while keeping cyber threats at bay.



